NYNOX OFFERS CYBERSECURITY AS A SERVICE
Last year, the number of cyberattacks increased by 32% and this number continues to rise. With these figures in mind, Nynox wants to take care of all of a company’s cybersecurity needs so that they can fully focus on their core business activities.
Built on years of experience and after many discussions with customers, Nynox has developed a unique strategy in the fight against cybercrime. By offering cybersecurity as a service, Nynox can focus on the three key levels: prevention, detection, and response.
Prevention
A solid protection against hacks and ransomware begins with a watertight prevention layer. There are several tools that can be used at this level, but Nynox focuses on two technologies that have a proven track record and offer great value for a performing prevention strategy: Vulnerability Management and the Endpoint Detection & Response tool.
Vulnerability Management
A good Vulnerability Management strategy is key. By clearly mapping vulnerabilities within the environment, necessary priorities can be given and low hanging fruit for cybercriminals can be eliminated. Hackers are naturally lazy, so if they have to put in too much effort, they quickly give up.
Endpoint Detection & Response (EDR)
A good EDR tool also plays a central role in the cybersecurity strategy. Traditional antivirus no longer suffices, to be able to fend off attacks in a timely manner, targeted actions must be taken at the endpoint level.
The question is not how, but when you will become the victim of a cyberattack. That is why it is also extremely important to invest in a good detection strategy. This brings us to the next service layer: detection.
DETECTION
Detection is Nynox’s core business. With our 24/7 available Security Operations Center (SOC), Nynox monitors the environment of many customers for potential cyber attacks. We do this by collecting logs from various critical log sources or security solutions. This information will be forwarded to our SOC solution where it will be correlated. Possible security alerts are then closely examined by our SOC engineers.
Of course, when you have detected a security threat, you also want a partner who takes the necessary action.
This brings us seamlessly to our next layer: response.
response
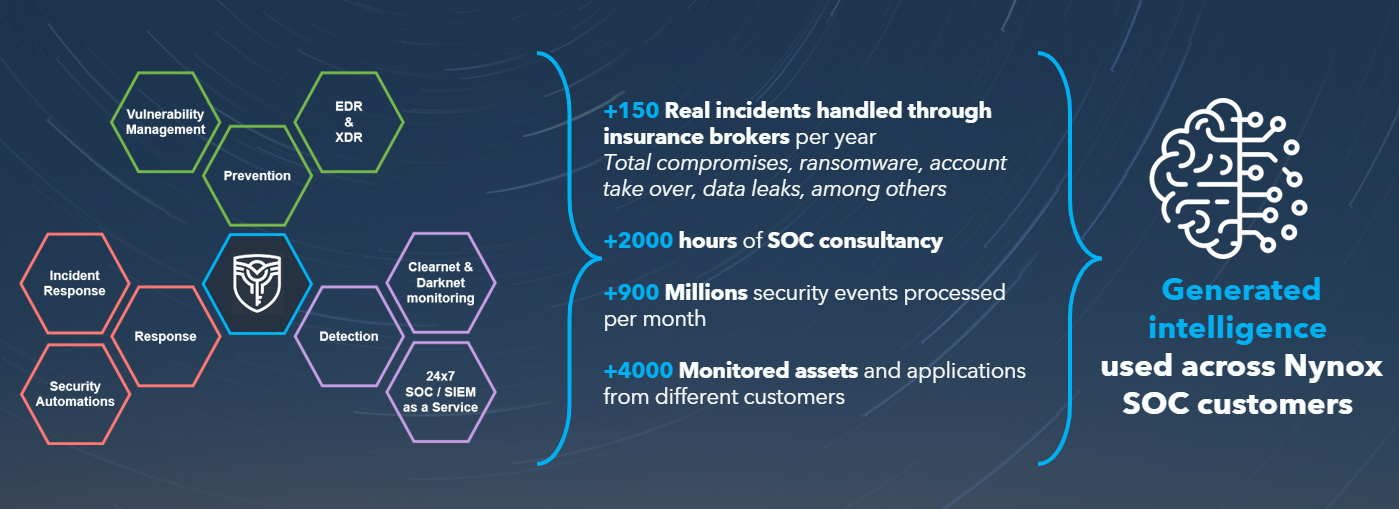
Nynox has a highly experienced and reliable Cyber Security Incident Response Team (CSIRT) that is ready to help our customers in case of a cyberattack 24/7. And the word ‘experienced’ can be taken literally: Nynox is also deployed as an independent SOC for various insurance companies. When an insurer is under attack, Nynox is called in to isolate the incident, conduct forensic investigations, draw up a report, and provide advice to avoid such incidents in the future. Thus, Nynox is involved in about 150 cyber incidents annually.
Here are some statistics:
WHAT to look for IN CHOOSING the right SOC PARTNER?
Find a real partner and not just a license seller because a magical box unfortunately does not exist in cybersecurity. It is not about the technology in cybersecurity, but about the services surrounding it. So, be sure to choose a partner with demonstrable experience and for whom defensive security services or blue teaming are truly their core business and core passion.
for your business?
Learn more

Incident response (CSIRT)
Deal with and fix all cybersecurity threats and incidents you might encounter, so you can concentrate on your core business and SW@N (Sleep Well @ Night)

Security Monitoring
Our round-the-clock managed Security Operations Center (SOC), built on a central logging service, helps you defend against cyberthreats. The core of our Blue Team service.

Endpoint protection
Endpoint protection secures endpoints or entry-points against potential threats and breaches. An endpoint in an IT infrastructure is any device that is connected to the network.
