Nynox's advisory - LOG4J Vulnerability Insights (CVE-2021-44228)
– Date: 11 December 2021 –
A critical vulnerability has been identified on a software component, Log4j, widely used in infrastructure of different vendors such as VMWare among many others. This vulnerability allows remote code execution on systems that use this piece of software. The vulnerability allows an attacker with a way to get a trivial text string message into the Log4J parser to inject JNDI interface commands when Log4J versions less than 2.15 are used.
The injected interface commands would let the attacker execute code remotely without authentication nor privilege at all.
The challenge with this threat is that there are numerous applications that use Log4J to record their events. For example, certain Check Point products use Apache SOLR, which uses Log4j.

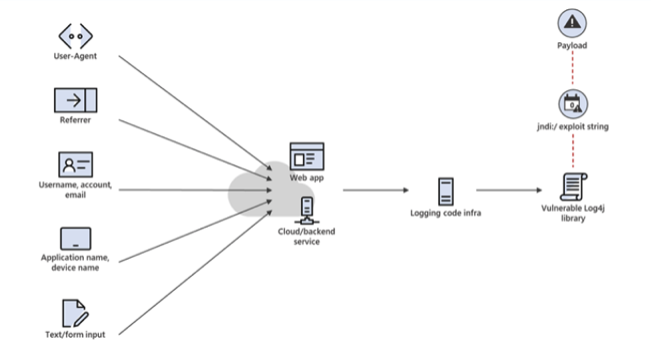
The following diagram provided by Microsoft shows the different ways that attackers can use to exploit the vulnerability.
From Nynox we have been monitoring the evolution of the vulnerability and estimating the impact analysis on different infrastructures and platforms that must be patched or those that must follow the alternative remediation process.
- We are researching and developing SIEM detection use cases to detect potential Log4j exploitation.
- Tenable has released a set of checks for Log4j. Contact Nynox if you need assistance in configuring the corresponding scanners.
More technical details of this vulnerability can be found at this link: https://nvd.nist.gov/vuln/detail/CVE-2021-44228
Recommendations
- Check if you are running vulnerable applications and contact your vendor or Nynox.
You may use the following list as guidance: Click here - Upgrade your affected applications to Log4j to version 2.15 as soon as possible.
- Public-facing applications have a greater risk, prioritize these first.
- In some cases, you may need to rely on vendor specific patches to mitigate the vulnerability.
- Check if your Intrusion Prevention System (IPS) or Web Application Firewall (WAF) has signatures for the Log4j vulnerability. It is important for you to know that your security appliance must be able to inspect TLS traffic for these signatures to work.




